Most people looking to get into cybersecurity have no idea what the correct roadmap is or what type of role they need to apply for. Some people don’t even know that there are so many different roles in the industry, while others are thinking about certifications.
If you also have these confusing thoughts, then I am going to talk about different roles in cybersecurity so that you can decide which role suits you the best.
What is Cybersecurity?
A lot of people think cybersecurity is just about hacking or hackers. Some people have maybe watched the Mr. Robot TV series and think, okay, cybersecurity is all about that. But the reality is there are actually different roles in cybersecurity that don’t even involve hacking. Some of them are not even technical; they’re not even IT-related.
Cybersecurity involves protecting systems, programs, and networks from digital attacks, commonly known as cyber-attacks. In cybersecurity, we have event awareness, security events, training laws, GRC, engineering, etc. Now, let’s look at some of the roles in cybersecurity.
Different Roles in Cybersecurity?
If you can see the image below, we have a “Red Team” on the right side, a “Blue Team” on the left side and a “Purple Team” in the middle between Red and Blue. On top of the Blue Team, we have GRC and Security Engineering. On the right side, at the top of the image, we have different roles that are not really technical, and some of them are even very niche targeted roles in cybersecurity. In this blog, we will cover the major roles in cyber security.
For convenience, we have categorized the cybersecurity roles into Red Team, Blue Team, and Purple Team. In addition to these, we have two more roles: GRC and Security Engineering. Let us know about these roles briefly.
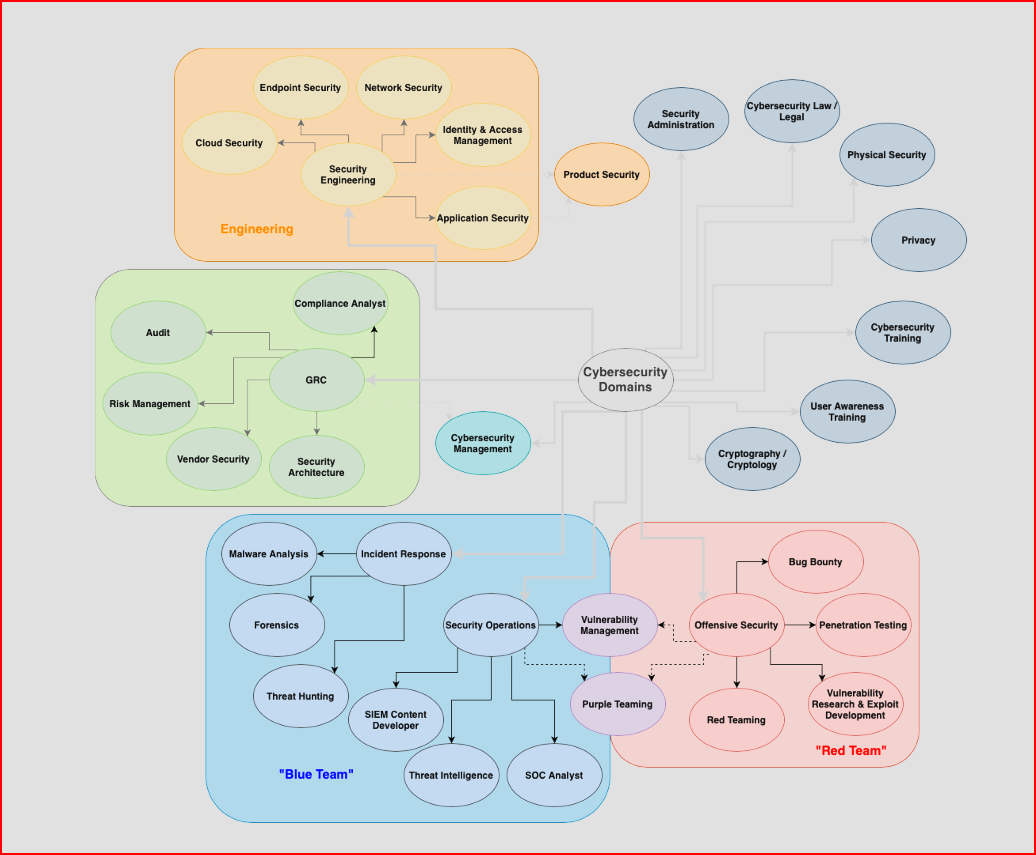
Red Team
So, let’s start with the Red Team. It is all about the offensive side, like mimicking how hackers operate to identify weaknesses in an organization’s defenses, how they perform their attacks, understanding the attacker’s behaviors, and creating exploits and malware. These roles actually help us understand how hackers work so we can put defenses in place. They include:
Offensive Security Analyst: Offensive security or OffSec Analysts use the same tactics and strategies used by cyber attackers to strengthen network security and improve defensive strategy. They mimic cyber-attacks to identify what are the potential weaknesses within an organization’s systems, networks, and applications.
This role is critical for understanding vulnerabilities from an attacker’s perspective, allowing the organization to strengthen its defenses before real-world attackers can exploit them.
Bug Bounty Hunting: While Bug Bounty Hunting is not a formal job position in cybersecurity, it is a freelance or contract-based role. Many companies run bug bounty programs, rewarding third-party security researchers or ethical hackers for finding and reporting vulnerabilities within their software or systems. This helps them identify and fix security flaws.
Penetration Tester: Companies use internal and external web applications intensively to conduct business operations smoothly. These applications are at risk of security breaches as they often use open-source plugins. A Penetration Tester mimics a malicious attacker and uses a variety of tools and techniques to simulate real-world attacks to bypass the security barriers of these applications and assess the security integrity of a company’s defenses.
Vulnerability Researcher & Exploit Developer: Just as prevention is better than cure, the same goes for cyber security. It is better to identify vulnerabilities and be prepared for them in the future than to respond to the vulnerabilities. This is where a Vulnerability Researcher & Exploit developer comes into the picture. They find vulnerabilities or threats in applications the company uses before the adversaries find and exploit them.
Red Teamer: The Red Teamer’s primary goal is to put itself in the shoes of an adversary. Then, it operates how it would operate in different situations and uses the same tactics, techniques, and procedures as them. It mimics a real attacker and tries to get specific sensitive information using stealth and speed. This role is created to test an organization’s ability to detect and respond to real threats and help make the Blue Team better.
Blue Team
Blue team is all about defending the organization from cyber threats, monitoring systems, and responding to incidents. They’re the first in line of defense. When something bad happens, they try to figure out what happened, who attacked first, and where the attack came from. This team has roles like Incident Responder, Malware Analyst, Forensics Analyst, and Threat Hunter. Some other job roles that fall under the Blue Team are Security Operations Engineer, SIEM Content Developer, Threat Intelligence Analyst and SOC Analyst.
Incident Responder: Incident Responders specialize in detecting and responding to cyber incidents. They focus on identifying, analyzing, and mitigating security breaches or threats in real-time. When a security attack has occurred, they will locate the attackers, use their quick thinking and technical skills to minimize their ability to cause further damage and eliminate them.
Malware Analyst: If you would like to reverse engineer a cyber attack to understand the nature of the threat, then the job of a Malware Analyst might be the right fit for you. They focus on understanding malicious software, such as how it got in, what it has done, or what it has the potential to achieve, to determine how it functions and how to protect systems from similar threats in the future.
Forensics Analyst: To determine the cause of an incident, Forensics Analysts gather and analyze digital evidence following a security incident. They also help trace the cause and origin of breaches and support investigations.
Threat Hunter: A Threat Hunter proactively searches for security threats within an organization’s network and looks for evidence of an attack not uncovered by traditional detection methods. They help uncover and address potential risks before they cause harm.
Security Operations Engineer: A Security Operations Engineer defends an organization’s infrastructure against threats and cyberattacks. They proactively manage security tools, monitor, detect, and respond to alerts within the Security Operations Center (SOC). Moreover, they prevent security incidents to ensure the data, systems and personal information are protected against all cyber threats.
SIEM Content Developer: An SIEM (Security Information and Event Management) Content Developer is responsible for developing, refining, and managing SIEM content, including alerts, rules, and correlation searches. They help companies remain highly effective against the constantly evolving nature of cyber threats.
This role is essential for maintaining the accuracy and relevance of SIEM alerts and for tuning the SIEM system to align with the organization’s unique security needs.
Threat Intelligence Analyst: This role involves detecting new cyber threats by collecting, analyzing, and interpreting information about potential or current threats, including indicators of compromise and threat actors. These analysts then report their findings to the security teams, predict similar attacks based on these findings and help prevent any future cyberattacks.
SOC Analyst: A Security Operations Center (SOC) Analyst has an eye for detecting anomalies. They monitor and investigate potential security incidents within the SOC and help the organization identify attacks quickly and remedy them before they cause major damage. The role of a SOC Analyst involves analyzing logs, detecting anomalies, and responding to alerts to protect the organization.
Purple Team
The Purple Team is a collaborative unit that ensures both the Red Team (offensive security) and the Blue Team (defensive security) work towards common objectives to enhance an organization’s ability to identify, mitigate, and respond to cyber threats more effectively. Unlike the Red and Blue Teams, which traditionally operate separately, the Purple Team’s primary role is to foster communication, coordination, and mutual learning between these two groups.
Vulnerability Management Analyst: To safeguard themselves from potential threats, businesses need to scan their assets and systems regularly for vulnerabilities. A Vulnerability Management Analyst does this work. He identifies, assesses, and mitigates security vulnerabilities within an organization’s IT infrastructure. This role is crucial for protecting systems, networks, and applications from potential threats that can be exploited by attackers.
Purple Teamer: Purple Teamer combines both Blue Team (defensive) and Red Team (offensive) tactics to improve an organization’s security posture. They coordinate to identify vulnerabilities, test defenses, and implement effective measures to mitigate risks. Individuals working as Purple Teamer are often involved in vulnerability management and cross-team exercises known as purple teaming.
GRC Analyst
GRC, or Governance, Risk, and Compliance Analyst, manages the overall security strategy and compliance obligations within an organization to ensure it meets government and industry compliance standards. For example, imagine that you’re living in a city with walls around it. There are soldiers on top of the walls, and they are the Blue Team responders. They’re there to defend the city. But we also need laws in the city to make sure it is well governed.
Certain people give you the law and force you to follow some rules and specific policies inside the city. The same is the case with companies. They need to have a set of policies and frameworks to make sure they comply with all government standards. So that’s the role of a GRC Analyst. They follow best practices in security governance, apply for necessary certifications, and work as subject matter experts in all compliance-related matters.
Security Engineer
The role of a Security Engineer is all about building secure systems, including firewalls, encryption algorithms, and network protections, designing them and making sure that they are configured properly. Further, they ensure that they are operating 24* and updated regularly. They work to ensure that systems are protected against attacks, meet organizational security requirements, and assist the IT team in developing solutions to avoid future security breaches.
Start Your Career in Cyber Security Today!!
Now, the important question is, which field in cybersecurity do you want to pursue? Is it the Red Team, the Blue Team, or the Purple Team? Security Engineering? Or is it GRC? The first step to getting started in cybersecurity is to decide your niche and the role that suits you the best.
After that, you can easily reverse engineer the role and find the tools that you need to learn the skills needed for that role. If you want to know more about how to get started in cybersecurity, check out this blog.